C++转shellcode的曲折历程
没有人响应,看来写的太滥了, 自己重新排一下版, 把原代码都粘上, 希望招徕几个看客...
第一次写类似的东西,实在是没有经验,历程非常坎坷,先后用了大约两个月时间,主要是因为我之前的电脑台垃圾了,6年前的笔记本 512MB内存,随便抛个调试器就快死机了,也没有太多心情搞那个,就一直拖了下来,直到换了新机才来完成这一遗留问题。
开始的目的是,我这里有一个dll 里面会暴露出两个方法, 同样进程中有多个这样的dll, 我的目的是获得其他dll对应函数的地址。 正常高级语言应该是没有这样的功能的,所以选择用pe表查询的方式。
// BWChess.cpp : Defines the entry point for the console application.
//
上面代码执行是没有问题的:
结果如图:

但是这些肯定不是最终目的,目的是用shellcode形式表达, 利用windbg反汇编指令 uf 对Searching函数反汇编结果如下:
利用ultraedit很容易将机器码提取出来, 放入char数组chsch中,
注释添加函数指针定义
然后编译执行, 发现程序崩溃, 仔细检查代码发现Searching函数中被编译器插入了若干安全检查函数:__security_cookie / !__security_check_cookie 和 _chkstk.
观察发现_chkstk是以简单源码形式存在的只要将原代码dump出来放入特定位置并在运行时适当修改chsch的内容即可,于是有了下面两个char数组
还需要一个函数在运行时修改chsch:
作了以上操作后,程序不在崩溃,但是也得不到希望的结果,于是开始了相对漫长的调试过程,由于先前的电脑实在不给力,工作就一直搁置了下来。。。
经过研究发现,编译器添加的关于安全cookie的代码可以删除,_chkstk应该也可以删除不过比较简单就没处理它,然后开始调试程序, 一直没什么进展,直到使用od里面的runtrace功能,获得了下面结果:
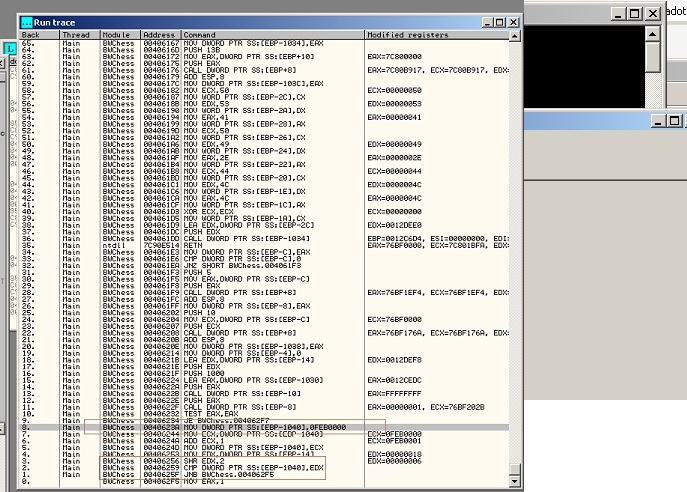
代码在执行地址0040625f时退出,而导致该处退出的是在0040623a处对ebp-1040位置的赋值0feb0000所导致。
而这部分正对应的是原代码中的
将chsch修改如下,则问题解决
结果:
最终整理后的代码大致如下
谢谢收看


