标 题: 【原创】用windows cryptoAPI写的HASH小工具(附asm源码)
作 者: zyr零零发
时 间: 2010-02-11
最近研究密码学,接触到windows cryptoAPI,我新学asm编程,就拿来练手,在此公布源码,愿意和ASM爱好者共同学习提高。借鉴了网上很多其他语言资料,尤其是MSDN。。。。在此一并感谢。。。。有什么改进的,就请高手就指点指点吧,如果您觉得不屑,就请飘过。
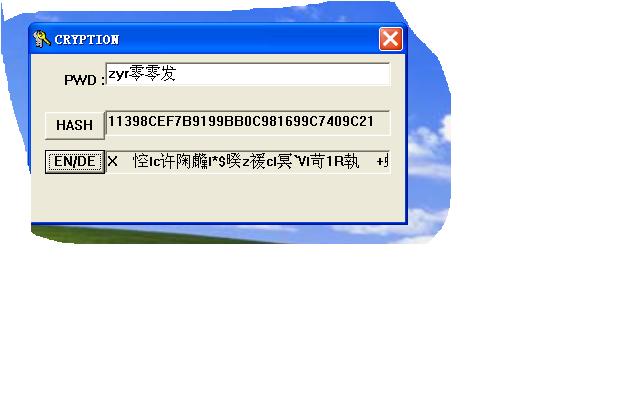
源码如下:
;Crypto API,For hashing,encrypting and decrypting,work on winXP xp3
;Author:ZYR零零发,
;Date:02/09/2010
;hashing:MD5
;Encrypting/Decrypting(STREAM CIPHER): RC4
;Use masm ver10.0
;For guidance from msdn and Tyg-'s work
.386
.model flat,stdcall
option casemap:none
;>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
include windows.inc
include user32.inc
include kernel32.inc
include advapi32.inc
include gdi32.inc
includelib user32.lib
includelib kernel32.lib
includelib advapi32.lib
includelib gdi32.lib
;>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
;等值定义
;>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
PKCS_7_ASN_ENCODING equ 00010000h
X509_ASN_ENCODING equ 00000001h
ALG_SID_MD5 equ 00000003h
ALG_SID_RC4 equ 00000001h ;stream cipher
ALG_SID_RC2 equ 00000002h ;block cipher
PROV_RSA_FULL equ 00000001h
HP_HASHVAL equ 00000002h
ALG_CLASS_ANY equ 00000000h
ALG_CLASS_SIGNATURE equ 00002000h ;(1 << 13) 10000000000000
ALG_CLASS_MSG_ENCRYPT equ 00004000h ;(2 << 13) 100000000000000
ALG_CLASS_DATA_ENCRYPT equ 00006000h ;(3 << 13) 110000000000000
ALG_CLASS_HASH equ 00008000h ;(4 << 13)1000000000000000
ALG_CLASS_KEY_EXCHANGE equ 0000A000h ;(5 << 13)1010000000000000
ALG_TYPE_ANY equ 00000000h
ALG_TYPE_DSS equ 00000200h ;(1 << 9) 1000000000
ALG_TYPE_RSA equ 00000400h ;(2 << 9) 10000000000
ALG_TYPE_BLOCK equ 00000600h ;(3 << 9) 11000000000
ALG_TYPE_STREAM equ 00000800h ;(4 << 9) 100000000000
ALG_TYPE_DH equ 00000A00h ;(5 << 9) 101000000000
ALG_TYPE_SECURECHANNEL equ 00000C00h ;(6 << 9) 110000000000
CRYPT_VERIFYCONTEXT equ 0F0000000h
CRYPT_EXPORTABLE equ 00000001h
CALG_MD5 equ ALG_CLASS_HASH OR ALG_TYPE_ANY OR ALG_SID_MD5
CALG_RC4 equ ALG_CLASS_DATA_ENCRYPT OR ALG_TYPE_STREAM OR ALG_SID_RC4
CALG_RC2 equ ALG_CLASS_DATA_ENCRYPT OR ALG_TYPE_BLOCK OR ALG_SID_RC2
IDC_EDIT1 equ 1001
ID_HASH equ 2001
IDC_EDIT2 equ 1002
ID_ENCRYP equ 2002
IDC_EDIT3 equ 1003
ID_DECRYP equ 2003
ICO_MAIN equ 1
DLG_MAIN equ 2
;>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
.const
szNo1 db 'hProv create unsuccessful!',0
szNo2 db 'hHash create unsuccessful!',0
szNo3 db 'hashdata unsuccessful!',0
szNo4 db 'gethash failed!',0
szNo5 db 'createkey failed!',0
szNo6 db 'encrypt failed!',0
szNo7 db 'decrypt failed!',0
.data?
hInstance dd ?
hProv dd ?
hHash dd ?
hKey dd ?
szBuffer db 128 dup (?)
;#################################################################################
.code
;!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
;It is convert BYTE to string
;_lenght,length of buffer that contain byte
; _lpbit,buffer that contain byte
;_lpstr,Accepted string converted from _lpbit,It must allocate memory enough
;the process written by a guy named Tyg-,I thanks very much.
;@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
_Btos proc _lenght,_lpbit,_lphexstr
pushad
mov ecx,_lenght
mov esi,_lpbit
mov edi,_lphexstr
@@:
mov al,byte ptr[esi]
and al,0F0h
shr al,4
.if al<=9
add al,"0"
mov byte ptr[edi],al
.else
sub al,10
add al,"A"
mov byte ptr[edi],al
.endif
inc edi
mov al,byte ptr[esi]
and al,0Fh
.if al<=9
add al,"0"
mov byte ptr[edi],al
.else
sub al,10
add al,"A"
mov byte ptr[edi],al
.endif
inc edi
inc esi
dec ecx
cmp ecx,0
jnz @B
mov byte ptr[edi],0
xor eax,eax
popad
ret
_Btos endp
_ProcDlgMain proc uses ebx edi esi hWnd,wMsg,wParam,lParam
local @szBuffer[128]:byte
local @szBuffer1[256]:byte
local @dwBufferSize,@dwPwdsize
mov @dwBufferSize,sizeof szBuffer
mov eax,wMsg
.if eax == WM_CLOSE
invoke EndDialog,hWnd,NULL
.elseif eax == WM_INITDIALOG
invoke LoadIcon,hInstance,ICO_MAIN
invoke SendMessage,hWnd,WM_SETICON,ICON_BIG,eax
invoke GetDlgItem,hWnd,ID_ENCRYP
invoke EnableWindow,eax,FALSE
.elseif eax == WM_COMMAND
mov eax,wParam
.if ax == ID_HASH
invoke GetDlgItemText,hWnd,IDC_EDIT1,addr @szBuffer,sizeof @szBuffer
mov @dwPwdsize,eax
invoke CryptAcquireContext,addr hProv,NULL,NULL,PROV_RSA_FULL,CRYPT_VERIFYCONTEXT
.if !eax
invoke MessageBox,NULL,addr szNo1,NULL,0
invoke ExitProcess,NULL
.endif
invoke CryptCreateHash,hProv,CALG_MD5,0,0,addr hHash
.if !eax
invoke MessageBox,NULL,addr szNo2,NULL,0
invoke ExitProcess,NULL
.endif
invoke CryptHashData,hHash,addr @szBuffer,@dwPwdsize,0
.if !eax
invoke MessageBox,NULL,addr szNo3,NULL,0
invoke ExitProcess,NULL
.endif
invoke CryptDeriveKey,hProv,CALG_RC4,hHash,CRYPT_EXPORTABLE,addr hKey
.if !eax
invoke MessageBox,NULL,addr szNo5,NULL,0
invoke ExitProcess,NULL
.endif
mov @dwBufferSize,sizeof @szBuffer1
invoke CryptGetHashParam,hHash,HP_HASHVAL,addr @szBuffer1,addr @dwBufferSize,0
.if !eax
invoke MessageBox,NULL,addr szNo4,NULL,0
invoke ExitProcess,NULL
.endif
invoke _Btos,@dwBufferSize,addr @szBuffer1,addr szBuffer
invoke CryptDestroyHash,hHash
invoke SetDlgItemText,hWnd,IDC_EDIT2,addr szBuffer
invoke GetDlgItem,hWnd,ID_ENCRYP
invoke EnableWindow,eax,TRUE
.else
.if ax == ID_ENCRYP
invoke CryptEncrypt,hKey,0,TRUE,0,addr szBuffer,addr @dwBufferSize,@dwBufferSize
.if !eax
invoke MessageBox,NULL,addr szNo6,NULL,0
invoke ExitProcess,NULL
.endif
invoke SetDlgItemText,hWnd,IDC_EDIT3,addr szBuffer
.elseif ax == ID_DECRYP
invoke CryptDecrypt,hKey,0,TRUE,0,addr szBuffer,addr @dwBufferSize
.if !eax
invoke MessageBox,NULL,addr szNo7,NULL,0
invoke ExitProcess,NULL
.endif
.endif
.endif
.else
mov eax,FALSE
ret
.endif
mov eax,TRUE
ret
_ProcDlgMain endp
start:
invoke GetModuleHandle,NULL
mov hInstance,eax
invoke DialogBoxParam,hInstance,DLG_MAIN,NULL,offset _ProcDlgMain,NULL
invoke CryptDestroyKey,hKey
invoke CryptReleaseContext,hProv,0
invoke ExitProcess,NULL
end start
encyrptoAPI.rar
- 标 题:【原创】用windows cryptoAPI写的HASH小工具(附asm源码)
- 作 者:zyr零零发
- 时 间:2010-02-11 16:53:53
- 链 接:http://bbs.pediy.com/showthread.php?t=107116