FCGбЇдБЧјзЪСЯЃЌзЊдиЧызЂУї
ФПБъЃКapis32 v 2.5ЃЌ
БЃЛЄЗНЪНЃКRSA8
вдЧА:ArchFire/ATAаДЙ§ЃЌЕЋФуПДСЫетЦЌЮФеТ
ПЩФмЛсгааТЕФЪеЛёЁЃ
СэвЛИіФПБъЃКWMV to AVI MPEG DVD WMV Converter 1.4.8
БЃЛЄЗНЪНЃКRSA256
http://www.alloksoft.com/wmv.htm
1.Brief Introduction to RSA
ШЁздRSA-Tool 2ЕФHelpЁЃ
1.1. About RSA
RSA
is a Public Key Cryptosystem
developed in 1977 by Ronald Rivest,Adi Shamir and Leonard Adleman.Since
1.2. Parameters
P = 1st large prime number
Q = 2nd large prime number (sizes of P and Q should not differ too much!)
E = Public Exponent (a random number which must fulfill :
GCD(E, (P-1)*(Q-1))==1)
N = Public Modulus, the product of P and Q: N=P*Q
D = Private Exponent: D=E^(-1) mod ((P-1)*(Q-1))
Parameters N and E are public whereas D is -private- and must NEVER be published! P and Q are not longer needed after keygeneration and should be destroyed.
To obtain D from the public key (N, E) one needs to try splitting N in its both prime factors P and Q. For a large Modulus N (512 bit and more) with carefully chosen primefactors P and Q this is a very difficult problem.
All the security of the RSA encryption scheme relies on that integer factorization problem (tough there's no mathematical proof for it).To find out more read here:
http://www.rsasecurity.com/rsalabs/challenges/factoring/rsa155.html
1.3. Encryption
To encrypt a messageblock (M) (which must be < N), compute:
Ciphertext = C = M^E mod N.
Note: If the entire message (M) is > N it must be split into smaller
blocks with size < N
1.4. Decryption
To decrypt a given Ciphertext (C) to retrieve the Plaintext (M) as result,
compute: M=C^D mod N. The ' ^ ' sign in the above equations means 'power of', not XOR !
Note that the RSA scheme does also work the other way round:
C=M^D mod N and M=C^E mod N. It's on you how you implement it. Just ALWAYS
make SURE that you -NEVER- publish the private exponent D, P and/or Q !
2.Make a keygen for apis32
v2.5
2.1 Tools used
ЁОDynamic DebuggerЁПOllyDBG v1.10 flyаоИФАц
2.2 Trace registration code checking routine
КУРВЃЌПЊЙЄЃЌгУODдиШыФПБъapis32.exeЃЌетИіГЬађЪЧМгПЧСЫЕФЃЌЕЏГіЯћЯЂПђЁАвЊМЬајЗжЮіТ№ЃПЁБЃЌбЁдёЁАЗёЁБЃЌЭЃСєдкШыПкЕуЃК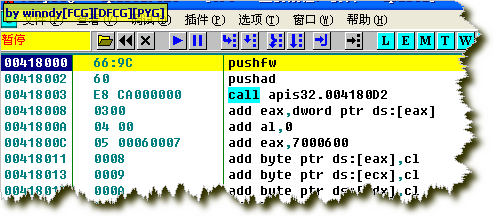
ЛуБржИСюзЂЪЭЃК
PUSHFW pushes
the bottom 16 bits of the flags register (or the whole flags register, on
processors below a 386) onto the stack.
PUSHAD pushes, in succession, EAX, ECX, EDX, EBX, ESP, EBP, ESI and EDI on the stack, decrementing the stack pointer by a total
of 32. The
value of SP or ESP pushed is its original value, as it had before
the instruction was executed.
етЪЧОпгабЙЫѕПЧЬиЩЋЕФПЊЭЗЃЌПЧЕФНсЮВБиЖЈЪЧгУpopadЃЌpopfwЃЌРДЛЙдМФДцЦїЁЃЯТУцЮвУЧОЭЫбЫїетСНЬѕжИСюЃЌctrl+S,ЫбЫї
Popad
Popfw
евЕНСЫЃК
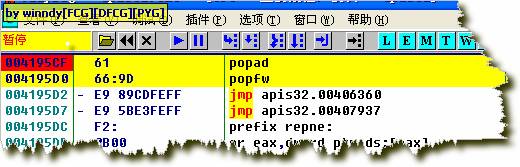
ЙтБъЭЃСєдкpopadФЧвЛааЃЌF2ЯТЖЯЕуЃЌдйF9дЫааЃЌжаЖЯдкpopadЃЌF7ЕЅВНЃЌжДааjmp 00406360ЃЌКѓЕНДяГЬађШыПкЕуЃК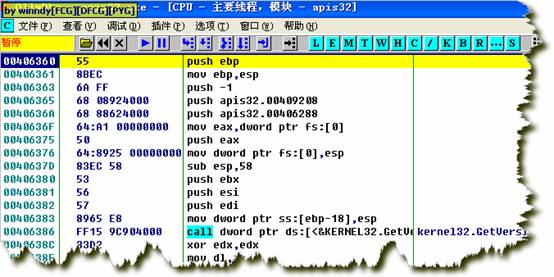
ШЛКѓгУOllyDUMPВхМўDumpГіГЬађЃЌRebuild importбЁЯюжабЁmethod 2ЃЌdumpГіЕФГЬађБЃДцЮЊaris32_unpacked.exeЃЌдЫааЃЌOKЁЃ
ЕНДяOEPЕФЕкЖўжжЗНЗЈ(ESPЖЈТЩ)ЃК
диШыapis32ЃЌЯТгВМўЖЯЕуЃКHR esp,(esp=0012FFC4)
F9дЫааЃЌжаЖЯдкЃК004195D2 - E9 89CDFEFF jmp apis32.00406360ЃЌетЪБзЂвтЙлВьЃК
ESPЃН0012FFC4.
гыЯТЖЯЕуЪБЕФespЯрЭЌЁЃетОЭЪЧЖбеЛЦНКтдРэЃЌбЙЫѕПЧдкдЫааНтбЙЕФГЬађЪБЃЌгІБЃжЄЖбеЛЕФАВШЋЃЌЗёдђГЬађЛсБРРЃЁЃ
зЂЪЭЃК
Hardware breakpoints or
BPM(Breakpoint on Memory) use the Debug Reg-
isters. In the archi-tectural
x86 (+386) 4 debug registers(DR0-DR3) exists in the processor. Sowe can
only set 4 BPM. The DR4 and DR5 are reserved registers, the DR6register
is for the debugger and the DR7 register still using for the type of
break for the DR0-DR3 registers.
ЭбПЧЭъБЯЃЌЯТУцОЭШЅИњзйЭбПЧКѓЕФГЬађЃЌзЗзйзЂВсТыЕФМьбщЙ§ГЬЁЃ
ЯШдкзЂВсДАПкЪфШыШЮвтгУЛЇУћКЭзЂВсТыЃЌПДЦфЬсЪОаХЯЂЃЌШЛКѓдйЫбЫїзжЗћДЎЃЌевЕНЬсЪОаХЯЂЃЌетбљОЭЖЈЮЛЕНзЂВсТыаЃбщЕФДњТыИННќСЫЁЃ
гвМќЃЌЫбЫїЃЌзжЗћДЎЃЌШЛКѓПДЕНШЋВПзжЗћДЎЃК
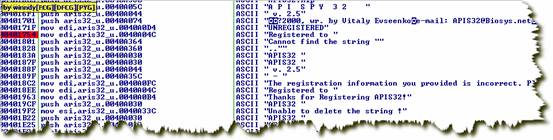
УєИазжЗћДЎецЖрАЁЃЁ
ШчЭМЃЌF2ЯТЖЯ,дйЫЋЛїЯТЖЯЕФФЧвЛааЃЌРДЕНГЬађжаЃЌЭљЩЯЗЃЌ
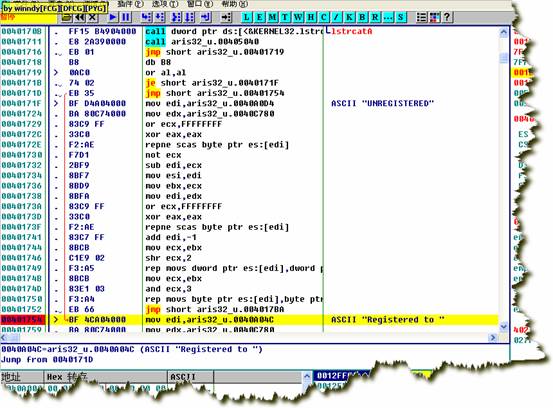
ПДКьЩЋЯпЃЌЪЧДгЩЯУц0040171DЬјЙ§РДЕФЁЃЩЯУцвЛОфЪЧjeЃЌШчЙћзЂВсТыаЃбщЪЇАмЃЌjeОЭЬјСЫЃЌзЂВсТыГЩЙІЃЌjeВЛЬјЃЌЯТвЛОфЬјЕН00401754ЁЃ
дйЭљЩЯПДЃК
00401711 |. E8
ЯдШЛЃЌетИіcallОЭЪЧгУРДМьбщзЂВсТыЕФЁЃЙтБъЭЃдк00401711етвЛааЃЌЛиГЕЃЌНјШыетИіcallЃЌ
дкетИіcallПЊЭЗЯТЖЯЕуЁЃ

жиаТдиШыЭбПЧКѓЕФГЬађЃЌНјШызЂВсДАПкЃЌЪфШыгУЛЇУћЃКwinndyЃЌзЂВсТыЃК1234567890
ЖЯдк00405040ЃЌжДааcall 00405370КѓЃЌЗЂЯжЃЌeaxЃН
ЭЌРэЃЌгУЛЇУћЕФГЄЖШвВвЊДѓгкЕШгк5ЁЃ
ИќИФзЂВсТыГЄЖШЮЊ16ЃЌ1234567890abcdefЃЌжиаТИњзйЁЃ
004050DA |. BE 41B74000 mov esi,aris32_u.0040B741
; ASCII "234567890abcdef"
004050DF |. BF 54B74000 mov edi,aris32_u.0040B754
; ASCII "123456780abcdef"
ДгетРяЮвУЧПЩвдПДЕНЃЌЕк9ИізжЗћБЛШЅЕєСЫЃЌвђДЫзЂВсТыИёЪНЮЊЃК12345678-90abcdefЁЃ
004050E4 |> 57
/push edi
004050E5 |. E8 E6010000 |call aris32_u.004052D0
=ЈЈМћЯТУц
004050EA |. 8ACB
|mov cl,bl ЃЛblЪЧМЦЪ§ЦїЃЌГѕжЕЮЊ0
004050EC |.
004050EF |.
004050FC |. C606 00 |mov
byte ptr ds:[esi],0
004050FF |. 46
|inc esi
00405100 |. 80FB 08 |cmp
bl,8
00405103 |.^ 72 DF
\jb short aris32_u.004050E4
004050E5ДІЕїгУЕФКЏЪ§ЃК
004052D0 /$ 8B
004052D4 |.
004052D6 |.
004052D8 |. 7E 04 jle short aris32_u.004052DE
004052DA |.
004052DC |. EB 02 jmp short aris32_u.004052E0
004052DE |> 04 D0 add
al,0D0
ЃЛ39ЃЋD0ЃН109
004052E0 |>
004052E3 |.
004052E6 |. 7E 09
jle short aris32_u
004052E8 |. C0E0 04 shl al,4
;зѓвЦ4ЮЛ
004052EB |. 80E9 37 sub cl,37
ЃЛ
004052EE |.
ЩЯУцетЖЮГЬађЕФЙІФмЪЧНВЪфШыЕФзЂВсТызжЗћДЎЃЌУПСНИізЊЛЏЮЊвЛИіbyteЃЌР§ЃКЁА
дйЭљЯТУцПДЁЃ
00405300 /$ 53 push ebx
00405301 |. 55 push ebp
00405302 |. 8B
00405306 |. 56 push esi
00405307 |. 57 push edi
00405308 |. 8B
0040530E |. 2BFD sub edi,ebp
00405310 |.
00405314 |. EB 04
jmp short aris32_u
00405316 |> 8B
0040531D |. 33D2 |xor edx,edx
00405324 |. C74424 14 07000>|mov dword ptr ss:[esp+14],7 //етЪЧбЛЗМЦЪ§Цї
//ШЁвЛИіbyteЃЌгЩзЂВсТыБфЛЛЖјРД
00405331 |> 8BD7
|/mov edx,edi
00405333 |. 0FAFC2 ||imul eax,edx
00405336 |. 3D 99880000 ||cmp eax,8899
0040533B |. 7E
0040533D |. 99 ||cdq
0040533E |. BB 99880000 ||mov ebx,8899
00405343 |. F7FB ||idiv ebx
00405345 |. 8BC2 ||mov eax,edx //Mod 8899ЃЌШЁгрЪ§
00405347 |> 8B5424 14 ||mov edx,dword ptr ss:[esp+14]
0040534B |.
00405350 |.^ 75 DF |\jnz short aris32_u.00405331
00405352 |. 99 |cdq
00405353 |. BF BB000000 |mov edi,0BB
00405358 |. F7FF
|idiv edi
0040535B |.
0040535E |. 8816 |mov byte ptr ds:[esi],dl //mod 0BBЃЌБЃДцгрЪ§
00405360 |. C60429 00 |mov byte ptr ds:[ecx+ebp],0
00405364 |.^
00405366 |.
00405367 |. 5E
pop esi
00405368 |. 5D pop ebp
00405369 |. 5B pop ebx
МЬајЭљЯТПДЃК
0040514B |.
0040514E |.
00405152 |. 73 30 jnb short aris32_u.00405184 ;ГЄЖШ<8ЪБЃЌВЙЕН8ЮЛ
00405154 |. 8B5424 10 mov edx,dword ptr ss:[esp+10]
00405158 |. BF C
0040515D |. 81E2 FF000000 and edx,0FF
00405163 |.
00405166 |.
0040516E |. F7D1 not ecx
00405170 |. 2BF9 sub edi,ecx
00405172 |. 8BC1 mov
eax,ecx
00405174 |. 8BF7
mov esi,edi
00405176 |. 8BFA
mov edi,edx
00405178 |. C1E9 02 shr
ecx,2
0040517B |. F3:A5 rep movs dword ptr es:[edi],dword pt>
0040517D |. 8BC8 mov ecx,eax
00405182 |. F3:A4 rep movs byte ptr es:[edi],byte ptr >
00405184 |> C605 66B74000 0>mov byte ptr ds:[40B766],0 ЃЛгУЛЇУћГЄЖШВЙзу8ЮЛСЫ
0040518B |. B9 54B74000 mov ecx,aris32_u.0040B754 ЃЛecxжИЯђзЂВсТыБфЛЛЖўРДЕФ8Иіbytes
00405190 |. BE 08000000 mov esi,8
00405195 |>
00405197 |.
00405199 |. 73 0E
|jnb short aris32_u
0040519B |. 33D2 |xor edx,edx ЃЛБъжОжБНгЧх0
0040519D |. 25 FF000000 |and eax,0FF
004051AB |. 25 FF000000 |and eax,0FF
004051B0 |.
004051B3 |. 33D0 |xor edx,eax
; БШНЯЃЌШчЙћedxЃНeaxЃЌЛсжУedxЮЊСу
004051B5 |> 03EA |add ebp,edx
; ebpБЃДцБШНЯНсЙћЃЌШчЙћУПДЮedxЖМЮЊ0ЃЌдђebpзюжевВЮЊ0
004051B7 |. 41
|inc ecx
004051B8 |. 4E
|dec esi
004051B9 |.^ 75 DA \jnz short aris32_u.00405195
004051BB |.
004051BD |.
004051BE |. 85ED test ebp,ebp ; ebpЮЊ0Т№ЃП
жСДЫЃЌећИіЫуЗЈИњзйЙ§РДСЫЁЃдкЯТУцвЛНкРяЃЌзмНсвЛЯТЫуЗЈЁЃ
2.3 algorithm summary
ЛиЙЫвЛЯТбщжЄЙ§ГЬЃК
1.зЂВсТыГЄЖШДѓгкЕШгк16
2.гУЛЇУћГЄЖШДѓгкЕШгк5ЃЌВЛзу8ЮЛЕФШЁгУЛЇУћЕФЧАМИЮЛНЋЦфВЙзуЕН8ЮЛЁЃ
3.КіТдзЂВсТыЕФЕк9ЮЛЃЌЕк9ЮЛЖЈЮЊ-.
4.вРДЮШЁзЂВсТыЕФСНЮЛЃЌБЃДцЮЊвЛИіbyteЃЌЮЊЗНБуЦ№МћЃЌЩшзЂВсТыЮЊЪЎСљНјжЦзжЗћ(ЕБШЛвВПЩвЛЮЊЗЧЪЎСљНјжЦзжЗћЃЌвђЮЊГЬађУЛгаШЅбщжЄ)ЃЌЧвзЂВсТыГЄЖШЮЊ17ЃЌИёЪНЮЊЃКXXXXXXXX-XXXXXXXXЁЃ
5.НЋ8ИіbytesвЛДЮгы50hЃЌЁ57hвьЛђЁЃ
6.ШЁГівЛИіbyteЃЌМЧЮЊmЃЌnЃНnЁСmЃЌnЕФГѕжЕЮЊ1ЃЌШчЙћnДѓгк8899HЃЌдђmod 8899HЃЌгрЪ§ИГИјnЁЃетбљбЛЗЦфДЮ7ДЮЁЃ
7.НЋbyte Mod 0BBhЃЌБЃДцгрЪ§ЁЃ
8.НЋетзюжеЕФ8ИіbytesгыгУЛЇУћЯрБШНЯЃЌШчЙћЯрЕШЃЌдђзЂВсГЩЙІЁЃ
дкЯТУцЕФСННкРяЃЌНЋгУСНжжВЛЭЌЕФЫМТЗРДзіГізЂВсЛњРДЁЃ
2.4 write a keygen :Searching Table
ШчКЮЧѓГіЩЯУцЫуЗЈЕФФцдЫЫуФиЃП
ЕЙзХЭЦЕМЁЃ
ИјЖЈвЛИігУЛЇУћЃЌШчwinndyЃЌШЁвЛИіbyteЃЌФбвдЧѓЕУзЂВсТыЯргІЕФвЛИіbyteЁЃвђЮЊЕк6ВНВЛКУЧѓФцЁЃЕЋДѓМвВЛвЊЭќСЫЕк6ВНШЁЕФЪЧвЛИіbyteЃЌзюЖрвВжЛга256ИіЃЌетбљОЭПЩвдВЩгУЧюОйЗЈЃК
ЖдгкДг0ЕН255ЕФетаЉbyteЃЌАДееЕк6КЭЕк7ВНЃЌНЋУПИіbyteЫљЖдгІЕФbyteЫуГіРДЃЌетбљПЩвдЕУЕНвЛИіЖдгІЕФБэИёЃЌШЛКѓИљОнгУЛЇУћЕФbyteзіЮЊindexЃЌВщевБэИёОЭПЩвдЕУЕНзЂВсТыЕФbyteЃЌШЛКѓдйгыЯргІЕФ50hЃЌ..ЃЌ57hвьЛђЃЌМДПЩЕУЕНзЂВсТыЁЃ
ЫМТЗЗЧГЃМђЕЅЁЃ
ЮвгУVBБрСЫМђЕЅЕФГЬађЃЌжЦзїСЫБэИёЃЌаДГіСЫзЂВсЛњЁЃЯъМћдДТыЁЃ
зЂВсЛњжаМгШыСЫxmвєРжЃЌЮЊДЫЃЌЛЈСЫЮвВЛЩйЪБМфЃЌзюКѓевЕНuFMODЃЌExcellentЃЁ
2.5 write a keygen :RSA
ШчЙћФуСЫНтRSAЃЌдђПЩПДГіЃЌЕк6ВНЪЕМЪЩЯЪЧRSAдЫЫуЁЃ
ВЮПМСЫ ArchFire/ATA
@
2.4НкЕФзЂВсЛњЪЧЮвздМКзіЕФЃЌКѓРДВЮПМПДбЉОЋЛЊЃЌВХЗЂЯжетЦЊКУЮФеТЁЃдкДЫжЎЧАЃЌЮвЮДНгДЅЙ§гУRSAЕФГЬађЃЌвВФбЙжАЁЃЁ
ЗЯЛАДђзЁЃЌЯТУцНщЩмRSA8ЃК
Ек6ВНЃКC=((M^7) mod 8899) mod 0bb=(M^7) mod 0bb, вђЮЊ 8899 mod 0bb=0
вђДЫДѓЪ§nЃН0BBhЁЃНЋnЗжНтЮЊСНИіЫиЪ§ЕФЛ§ЃЌnЃН11*0B,p=11h,q=0Bh,
f=(p-1)*(q-1)= 10*
МДЮЊЧѓeЕФФЃФц(mod f).еташвЊгаЪ§ТлЕФжЊЪЖЃЌ
ЯТУцИјГівЛИіР§згЃЌЪжЙЄгУеЗзЊЯрГ§ЗЈЧѓФЃФцЃЌЪЕМЪжаЃЌгУteЃЁЕФRSAЃToolПЩвдМЦЫуГіdЃЌИНТМжаЛЙИјГіЦфЫќЯрЙизЪСЯЃК
КУСЫЃЌБОР§жаЃЌЮвУЧЕФdЮЊЃКd=17hЁЃгааЫШЄЕФПЩвдШЅЫувЛЯТЃЌМгЩюРэНтЁЃ
гкЪЧЃЌгЩгУЛЇУћЧѓзЂВсТыЕФЙ§ГЬМДЮЊЃК
M=(C^17) mod 0BBh
ЯъМћзЂВсЛњдДТыЃЌгыЧюОйЗЈБШНЯвЛЯТЃЌКУКУЬхЛсЁЃ
2.6 Some Questions and Assignment
1.ГЬађжаВЂУЛгаЖдЪфШыЕФbyteзївЊЧѓЃЌЪЕМЪRSAЫуЗЈгІЪЙCаЁгк0BBhЃЌвђДЫЮвУЧЕФзЂВсТыВЛЪЧЮЈвЛЕФЃЌетЪЧЮвЭЈЙ§ЧюОйЗЈЗЂЯжЕФЁЃИјГівЛИіР§згЃК
Winnhijk
7B
B
B
B
ЮвУЧдкЧѓЕУMКѓЃЌMЪЧаЁгк0BBhЕФЃЌЪТЪЕЩЯШчЙћЮвУЧНЋMМгЩЯ0BBhЃЌШчЙћMШдаЁгк256ЃЌМДШдЮЊвЛИіbyteЃЌМЬајВЮМгКѓУцЕФxorдЫЫуЃЌЕУЕНЕФзЂВсТыШдЪЧе§ШЗЕФЁЃ
дкЗНЗЈ1ЃЌгЩЧюОйЕУЕНЕФБэИёжаПЩвдКмУїЯдЕиПДГіРДЁЃ
2.ИљОнбщжЄЙ§ГЬЃЌзЂВсТыГЄЖШДѓгкЕШгк16ЖМЪЧПЩвдЕФЃЌЖјЧвШЅЕєЕк9ИізжЗћКѓЕФзЂВсТыИіЪ§вВВЛвЛЖЈЮЊХМЪ§ЃЌзЂВсТывВВЛвЛЖЈвЊЮЊ16НјжЦзжЗћЃЌЪдЯывЛЯТЃК
ПМТЧАбзюКѓСНИізжЗћЛЛГЩвЛИіЗЧ16НјжЦзжЗћЃЌБШШчzЃЈasciiЮЊ7AhЃЉЃЌ7Ah+C9h=143,гЩzЧѓЕУЕФalЕШгкЖрЩйЃПzДњЬцФФСНИі16НјжЦзжЗћЃПЧыЯТШЅздМКГЂЪдвЛЯТЁЃЃЈД№АИЪЧF0ЃЉ
F0 xor 57ЃНA7 ЃЌA7ЈDЈD>28ЃЈ(ЃЉ
Winnhij(
7B
ЗДжЎЃЌИјГіСНИіЪЎСљНјжЦзжЗћЃЌЦфЖдгІЕФЗЧЪЎСљНјжЦзжЗћДцдкТ№ЃПШчЙћДцдкЃЌЪЧЖрЩйЃП
3.ЧыгУЦфЫћБрГЬгябдЃЌаДГізЂВсЛњЁЃ
4.зЂВсТыБЃДцдкзЂВсБэжаЃКHKEY_LOCAL_MACHINE\SOFTWARE\APIS32
ЩЯУцЪЧRSA8ЃЌМгУмЕФУїЮФЪЧ8bytesЃЌЯТУцРДПДвЛИіRSA256ЃЌМгУмЕФЪ§ЪЧ256ИіbitsЃЌПДзївЛИі256НјжЦЕФЪ§ЁЃдкФкДцжага32ИіbytesЃЌИпЮЛдкКѓЃЌЕЭЮЛдкЧАЃЌетвЛЕуЮёБивЊЧхГўЁЃ
3.Make a keygen for WMV
to AVI MPEG DVD WMV Converter v1.4.8
3.1 Tools used
ЁОDynamic DebuggerЁПOllyDBG v1.10 flyаоИФАц
ЁОOtherЁП RSA-Tool 2 v17 by tE! [TMG]
PPSIQS V1.1 by Satoshi Tomabechi 2001
PPSIQS V1.1 download URLЃКhttp://www.asahi-net.or.jp/~KC2H-MSM/cn/
3.2Trace registration code checking routine
диШыWMV to AVI MPEG DVD WMV Converter.exeЃЌетИіГЬађЪЧУЛгаМгПЧЕФЁЃ
ЪзЯШЪфШыwinndyЃЌ1234567890ЃЌПДПДЬсЪОаХЯЂЁЃ

гвМќЃЌЫбЫйЃЌзжЗћДЎЃК
ПДЕНДэЮѓЬсЪОзжЗћДЎСЫАЩЃПРЯЙцОиЃЌЯТЖЯЁЃ
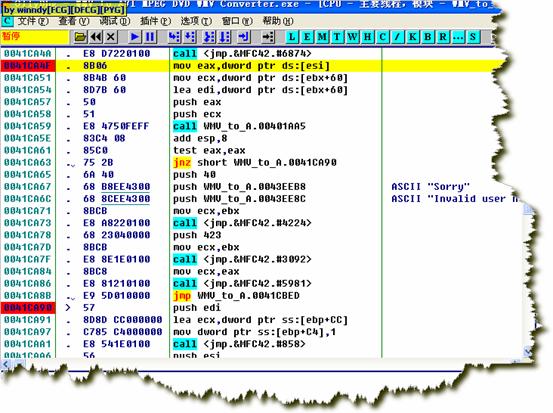
зЂвт0041CA63ДІЕФjnzЃЌЧАУц0041CA59ДІЕФcallОЭЪЧзЂВсТыбщжЄЙиМќВПЗжЁЃ
дк0041CA
ЭЌРэЃЌЩЯУцвВЯТЖЯЁЃ
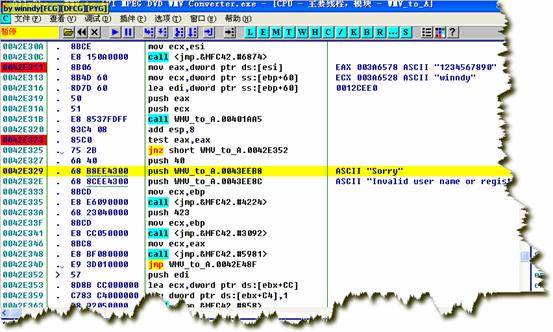
ЪфШыМйзЂВсТыКѓЃЌЭЃСєдк0042E311ЁЃ
F7НјШы00401AA5ЃК
00401AA5 $ /E9
зЂвтЩЯУцетаЉdwordЃЌвЛЙВ256ИіbitsЃЌзщГЩДѓЪ§nЁЃ
D esp+60
ЯТУцЪЧФкДцжаЕФЪ§ОнЃК
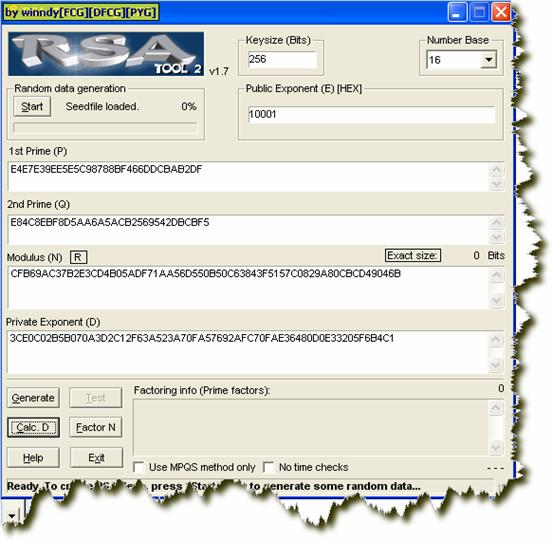
RSA256ЃЌетЪЧ256НјжЦЪ§ЃЌЕЭЮЛдкЧАЃЌИпЮЛдкКѓЃЌ NЃНCFB РћгУRSAЃToolНЋЦфзЊЛЏЮЊЪЎНјжЦЪ§ЃК
93951393961625247111454448822519571285412527322314031847324223587660098765931 вВаэгаШЫвЊЮЪЃЌОПОЙЪЧдѕУДЪЖБ№ЫуЗЈЮЊRSA256ЕФЃЌетжївЊППОбщСЫЃЌЪзЯШашвЊЪьЯЄИїжжМгУмЫуЗЈЃЌСЫНтИїжжЫуЗЈЕФГЃЪ§ЃЌЦфДЮЛЙвЊзЂвтЙлВьЬиеїЁЃЖМВЛааЪБЃЌЛЙЕУППТ§Т§ЗжЮіЃЌеташвЊгаКмДѓЕФФЭаФЁЃ
;зЂвтетвЛОфЃЌетвВЪЧRSAЕФвЛИіЬиеїЃЌE = Public
ExponentЃЌEвЛАуЕШгк10001HЁЃ зЂвтетИіИёЪНЛЏзжЗћДЎЃЌетвВОЭЪЧзЂВсТыЕФИёЪНЁЃ ЫљвдЯТДЮОЭАДеезЂВсТыЕФе§ШЗИёЪНРДЪфШыМйзЂВсТыЃК 12345678-90abcdef-12345678-90abcdef-12345678-90abcdef-12345678-90abcdef ОЙ§БфЛЛКѓЕФзЂВсТыЮЊЃК ПЩвдПДЕНЕк7ИіdwordКЭЕк8ИіdwordБфСЫЁЃЩшЕкiИіdwordЮЊcode(i), Code(8)= (code(5)+code(4)+code(3)+code(2))
Xor code(8) code(7) =(code(1)+code(6))
xor code(7) ЯТУцОЭгУRSA256ЖдетИі256НјжЦЪ§НјааНтУмЃЌНтУмГіРДЕФЪ§ОнОЙ§ИпЕЭЮЛзжНкНЛЛЛКѓЃЌЪЧгУЛЇУћЃЌдђзЂВсГЩЙІЁЃ ОЙ§етИіcallжЎКѓЃЌзЂВсТыЪ§ОнЧјБфЮЊЃК D ЭЈЙ§ЙлВьЃЌЩЯУцетИібЛЗНЋвЛИіdwordЕФИпЕЭзжНкНЛЛЛЁЃ БфЛЛЮЊЃК D ecx ЙиМќЕФБШНЯЃЌзЂВсТыгЩRSAНтУмЃЌгыгУЛЇУћНјааБШНЯЁЃ ЯждкЛиЙЫвЛЯТзЂВсТыЕФбщжЄЙ§ГЬЃК 1.зЂВсТыИёЪНЮЊЃК 12345678-90abcdef-12345678-90abcdef-12345678-90abcdef-12345678-90abcdef 2.зЂВсТыЕФЕк7ЖЮКЭЕк8ЖЮвЊгЩЧА6ЖЮРДаоИФЁЃ 3.аоИФКѓЕФ256bitsЪ§ОнЃЌОRSAНтУмЃЌЕУЕНвЛИі256bitsЪ§ОнЁЃ 4.ДЫ256bitsЪ§ОнЕФdwordИпЕЭЮЛНЛЛЛЃЌНЛЛЛКѓШчЙћЕШгкгУЛЇУћЃЌдђзЂВсГЩЙІЁЃ жЊЕРЫуЗЈвдКѓЃЌЯТУцОЭРДаДзЂВсЛњЃЌЮвгУЕФБрГЬгябдЮЊWin32ASMЃЌБрГЬЙЄОпЃКMASMV8.2ЁЃ зюФбЕФОЭЪЧДѓЪ§NЕФЗжНтЃЌNЃНp*q, RSA-ToolЗжНтЬЋТ§ЃЌзюКУЕФЙЄОпЪЧPPSIQS V1.1 by Satoshi Tomabechi 2001ЁЃ ОЙ§1ИіаЁЪБЖрвЛЕу(P4 93951393961625247111454448822519571285412527322314031847324223587660098765931
= P39 * P39 P39 = 304268020309461933344817079717793018591 P39 = 308778404861838864852708240341186890741 ДђПЊRSA-Tool ЃЌНЋЫќУЧзЊЮЊЪЎСљНјжЦЪ§ЃК E4E7E39EE5E (304268020309461933344817079717793018591) E (308778404861838864852708240341186890741) МЦЫуDЃК DЃН3CE ЃН27535870961668946496129164486976149735850411661692136930155875617194596807873 РћгУC=M^D mod N БуПЩвдМЦЫузЂВсТыСЫЁЃ ЛЙЪЧЕЙЭЦЁЃ гУЛЇУћЮЊ256bitsЪ§ОнЃЌ АбгУЛЇУћЕФasciiТыУПИіdwordОЙ§ИпЕЭзжБфЛЛЃЌБЃДцЮЊMЁЃ ШЛКѓЕїгУC=M^D mod NЃЌМЦЫузЂВсТыCЃЌCЕФЕк7ЖЮКЭЕк8ЖЮдйОЙ§XorДІРэЃЌдйгУИёЪНЛЏзжЗћДЎЪфГіЃЌМДЮЊзЂВсТыЃК "%08lX-%08lX-%08lX-%08lX-%08lX-%08lX-%08lX-%08lX"ЃЌЙигкwsprintfКЏЪ§ЃЌМћИНТМЁЃ зЂВсЛњВЩгУСЫbiglib v.0.01e by fleurЁЃИааЛзїепЃЁ зЂВсТыБЃДцдкdata.iniЮФМўжаЃЌЖСШЁзЂВсТыЃКGetPrivateProfileStringЃЌаДШызЂВсТыЃКWritePrivateProfileStringЁЃШєгУЛЇУћЧАКѓгаПеИёЃЌПЩвдзЂВсГЩЙІЃЌЕЋЪЧЯТДЮдЫааЪБШдЬсЪОЮДзЂВсЁЃдвђдкгкGetPrivateProfileStringКЏЪ§ЃЌКіТдСЫзжЗћДЎЧАКѓЕФПеИёЁЃ
заЯИЬхЛсвЛЯТЃЌЪЧШчКЮЪЖБ№ГіRSAЫуЗЈЕФЃЌР§згжаЃЌЪЖБ№ГіЫуЗЈКѓЃЌКмЖрcallЕФЙІФмЖМВЛСЫНтЃЌЕЋЭЈЙ§ЙлВьЪ§ОнЧјЕФБфЛЏЃЌШдаДГіСЫзЂВсЛњЁЃЪТЪЕЩЯЃЌЖдгкБъзМЫуЗЈЃЌР§ШчЃЌMD5ЕШЃЌЭЈГЃЖМЪЧППЪЖБ№ГіЬиеїЃЌШЛКѓаДГізЂВсЛњЕФЁЃМДЪЙПДMD5ЕФИпМЖгябддДТывВКмРЇФбЃЌИќВЛгУЫЕШЅПДЛуБрАцЕФСЫЃЌЫљвдЪьЯЄИїжжБъзМЫуЗЈЕФЬиеїЪЧКмЙиМќЕФЁЃ
гааЫШЄЕФПЩвдШЅГЂЪдНјШыcallИњзйвЛЯТЃЌПДФмВЛФмПДЖЎФГИіcallЕФЙІФмЃЌдйгУИпМЖгябдЪЕЯжжЎЁЃ
ЛЙгавЛИіШЮЮёЃЌЧыГЂЪдгУЦфЫћгябдаДГізЂВсЛњЁЃСэЭтЃЌЭјЩЯгаИіmiraclПтЃЌШЋГЦЪЧMIRACL -
Multiprecision Integer and Rational Arithmetic C LibraryЁЃ
БОЮФНщЩмСЫгУRSAЫуЗЈБЃЛЄЕФШэМўЕФЦЦНтЗНЗЈЁЃДгМђЕЅЕФRSA8ЕНИДдгЕФRSA256ЃЌВЂЧвИјГіСЫRSA8ЕФЧюОйЗНЗЈЁЃЛЙНщЩмСЫRSA-Tool 2 by te! [TMG]ЕФЪЙгУЗНЗЈЃЌвдМАРћгУppsiqs v1.1ЗжНтДѓЪ§ЁЃЛЙНщЩмСЫOllyDBGЖЏЬЌЕїЪдЙЄОпЕФЛљБОЪЙгУЗНЗЈЁЃЮЊСЫВЙГфЪ§ТлЕФжЊЪЖЃЌЛЙИјГіСЫвЛИіЪжЖЏЧѓФЃФцЕФР§ЬтЁЃ ИНТМвЛЃК EuclidЫуЗЈ http://zhdf.blog.edu.cn/user2/52478/archives/2006/1073022.shtml НёЬьдкПДRSAМгУмЫуЗЈЕФЪБКђПДЕНСЫПЩвдгУРЉГфЕФeuclidЫуЗЈРДМђЛЏdЕФМЦЫуЁЃвЛВщВХЗЂЯждРДeuclidЫуЗЈЫуЗЈОЭЪЧЯТУцетИіЪНзгЃК GCD
(a, b) = GCD (b, a % b) ЯТУцетИіЪЧжјУћЧѓзюДѓЙЋдМЪ§ЕФеЗзЊЯрГ§ЫуЗЈЕФДњТыЪЕЯжЃК int Euclid_Algorithm (int m, int n) if (!m || !n)
return 0; while (1) { ЖјРЉеЙЕФeuclidЫуЗЈЕФдРэЪЧетбљЕФЃК k*k-1=1(mod 26) k-1НаkЕФФЃФц, ПЩвдгУРЉеЙЕФEuclidЫуЗЈЧѓГіРДЁЃ ax = 1 (mod 26)
Цфжаx = a-1 ЯрЕБгк ax + by = 1ЃЌb = 26ЃЌЧѓТњзуЬѕМўЕФвЛзщx, yЁЃЕБШЛЮвУЧжЛвЊxОЭКУ. ЯждкПМТЧвЛАуЕФ ax + by = 1 ШчКЮЧѓНтЁЃ вђЮЊТњзуЬѕМўЕФx, yДцдкЕФЬѕМўЪЧGCD(a,
b) = 1. ШЛКѓга ax + by = GCD (a, b) ЖјЭЌЪБга bx' + (a % b)y' = GCD (b, a % b) гЩEuclidЖЈРэGCD (a, b)
= GCD (b, a % b) Ыљвд, гаax + by =
bx' + (a % b)y'= bx' + (a - [a/b]*b)y'= bx' + ay' - [a/b]*b y'= ay' + b(x'
- [a/b]y') ЖдгІ, ЕУx = y'ЃЌy = x' - [a/b]y'ЁЃ[a/b]ЪЧa/bдйШЁећЁЃ ЬиБ№ЕФ, дкb = 0ЕФЪБКђ, GCD (a, b) = a = a * 1 + b * 0 МД x = 1, y = 0 Ъ§ТлЖдгкКмЖрЫуЗЈПДРДЛЙЪЧКмгагУЕФЁЁ ИНТМЖўЃК sscanf <stdio.h> int sscanf(
const char *buffer,
const char *format [,
argument ] ... ); Parameters buffer Stored data format Format-control string. For more information,
see Format Specifications. argument Optional arguments Return Value Each of these functions returns the number
of fields successfully converted and assigned; the return value does not
include fields that were read but not assigned. A return value of 0 indicates
that no fields were assigned. The return value is EOF for an error or if
the end of the string is reached before the first conversion. Remarks The sscanf function reads data from buffer
into the location given by each argument. Every argument must be a pointer
to a variable with a type that corresponds to a type specifier in format.
The format argument controls the interpretation of the input fields and
has the same form and function as the format argument for the scanf function.
If copying takes place between strings that overlap, the behavior is undefined. Format Specification Fields: scanf and
wscanf Functions A format specification has the following
form: %[*] [width] [{h | l | I64 | L}]type The format argument specifies the interpretation
of the input and can contain one or more of the following: White-space characters: blank (' '); tab
('\t'); or newline ('\n'). A white-space character causes scanf to read,
but not store, all consecutive white-space characters in the input up to
the next nonЈCwhite-space character. One white-space character in the format
matches any number (including 0) and combination of white-space characters
in the input. NonЈCwhite-space characters, except for
the percent sign (%). A nonЈCwhite-space character causes scanf to read,
but not store, a matching nonЈCwhite-space character. If the next character
in stdin does not match, scanf terminates. Format specifications, introduced by the
percent sign (%). A format specification causes scanf to read and convert
characters in the input into values of a specified type. The value is assigned
to an argument in the argument list. The format is read from left to right.
Characters outside format specifications are expected to match the sequence
of characters in stdin; the matching characters in stdin are scanned but
not stored. If a character in stdin conflicts with the format specification,
scanf terminates, and the character is left in stdin as if it had not been
read. When the first format specification is
encountered, the value of the first input field is converted according to
this specification and stored in the location that is specified by the first
argument. The second format specification causes the second input field
to be converted and stored in the second argument, and so on through the
end of the format string. An input field is defined as all characters
up to the first white-space character (space, tab, or newline), or up to
the first character that cannot be converted according to the format specification,
or until the field width (if specified) is reached. If there are too many
arguments for the given specifications, the extra arguments are evaluated
but ignored. The results are unpredictable if there are not enough arguments
for the format specification. Each field of the format specification
is a single character or a number signifying a particular format option.
The type character, which appears after the last optional format field,
determines whether the input field is interpreted as a character, a string,
or a number. The simplest format specification contains
only the percent sign and a type character (for example, %s). If a percent
sign (%) is followed by a character that has no meaning as a format-control
character, that character and the following characters (up to the next percent
sign) are treated as an ordinary sequence of characters, that is, a sequence
of characters that must match the input. For example, to specify that a
percent-sign character is to be input, use %%. An asterisk (*) following the percent
sign suppresses assignment of the next input field, which is interpreted
as a field of the specified type. The field is scanned but not stored ЈDЈDЈDBy windyЁОFCGЁПЁОDFCGЁПЁОPYGЁП
ЈDЈDЈD2006.3.10ЭъИх
IЭЫ
3.3 algorithm summary
3.4 write a keygen :RSA

3.5
Some Questions and Assignment
4.Conclusion
5.appendix
{
int temp = m;
if (m < n)
{m = n; n = temp;}
if (!(m = m % n)) return n;
if (!(n = n % m)) return m;
}
}